There is a chaotic mess of different methods and systems in place across the United States for casting a vote, all of which are vulnerable to being hacked, some so much so that it makes zero sense to hold another election in the United States – until the system is fixed.
The list of statistics below provides a quick, high level glimpse of some of the glaring vulnerabilities in the US voting system. It is followed by a more detailed list of the ways each method used for casting and counting the votes in US elections can be manipulated.
EYE OPENING STATISTICS
OK. Let’s start off the bat with some frightening, eye-opening statistics.
- Every electronic voting machine used in US elections is vulnerable to hacking, even the ones not hooked directly to the Internet. (Learn more: “If Voting Machines Were Hacked, Would Anyone Know?.”)
- In 2012, as many as 39% of US voters could use e-voting machines for voting.
- Five states in the US use e-voting machines exclusively and most US states use e-voting machines to varying degrees. (Learn more: “America’s Electronic Voting Machines Are Scarily Easy to Hack.”)
- Most e-voting machines being used in US elections are out of date. Forty-three states are said to be using equipment that is 10+ years old and fourteen states are using equipment that is 15+ years old. Some of the voting machines used in US elections rely on software that is no longer being supported, making them extremely vulnerable to cybersecurity threats. (Learn more: Brennan Center for Justice).
- Security experts agree 99% of America’s votes are counted by computers.
- Five US States exclusively use a method of voting that has no verifiable paper trail and in as many as 15 states across the US, a percentage of voters use a voting method that provides no paper trail. It is impossible to verify if election fraud is committed, when there is no paper trail.
- At least 22 US States have provisions allowing for or mandating that certain or all statewide elections must be conducted entirely by mail. Voting-by-mail is a method of voting that is fraught with vulnerabilities at nearly every level. (Learn why in the section titled “Vote-by-Mail” below.)
- A total of 32 states allow some portion of voters to send in marked ballots via a web-based-portal, email, or fax — all of which experts have deemed to be insecure means of communication.
- As of 2012, approximately 56% of US voters could cast a vote using optical scan voting machines. These machines can be hacked in several different ways. (Learn more in the section titled “Optical Scan Voting” below.)
- Sixteen of our states have no legal statute for performing post-election audits. This means elections in these states could be hacked and nobody would ever know! Additional states like Pennsylvania and Kentucky have a statute requiring post-election audits be performed, but the elections are conducted using a voting method that doesn’t produce a voter-verifiable paper trail, so there is no way to actually complete the audit. Really?!
It is highly likely that your eyebrows went up when you read through the list of statistics above – as they should. This is by no means a comprehensive list of the problems. But, it should be more than enough to elicit a “Whoa, Nelly!” followed by a few choice expletives and more importantly an understanding that it is not possible to prove with any degree of certainty that the outcome of elections held in the US are legitimate – especially in regards to federal elections that rely on a combined vote tally from ALL of the elections held across our country.
Individual states across our country will of course all loudly continue to proclaim they can manage elections independently. Really?! Where’s the proof? The list above shows exactly otherwise. Our country engages in disturbingly chaotic elections every two to four years, riddled with glaring problems…and nothing is done to fix them because once an election ends, everyone understandably moves on to other pressing things. We know our elections are being targeted by other countries. Now is time to stop ignoring the problems and fix them.
Let’s fix our elections American-style! Let’s wipe the slate clean, start fresh, and create the best, most admired election system in the world. Sound daunting? It’s not. Nearly everything required to fix the elections exists in full already. Most of the best solutions for fixing our elections are actually incredibly simple. The simpler and more streamlined each component is, the safer the elections will be, making them simultaneously easy to monitor and impossible to hack. Our elections are a mess right now because we made them a mess, not because they have to be that way!
As it stands, NOT one of the 50 states across our country, who all loudly love to proclaim they can handle their own elections, conducts elections using a secure means of casting and counting the vote. If there is no way to prove the outcome is valid, pray tell — what exactly is the point of holding of holding the election at all?
In order for us to identify and come to a consensus on the best solution for keeping the votes cast secure, it is first helpful to have a basic understanding of how the existing voting methods being implemented across the United States are insecure. An outline of how each of the voting methods being used in American elections can be manipulated is presented below.
*Spoiler Alert!* EVERY voting method being used in US elections can be manipulated in not just one way, but in many different ways! As you read down through all the ways each of the voting methods are insecure, you might feel inclined to toss up your hands and completely give up hope. Don’t! A remarkably simple, fraud-proof voting method actually does exist. It is touched upon in the discussion below and covered in more detail on the proposed “Solution”page for addressing this problem, namely: how to keep the votes cast secure.
But first off, we definitely don’t want to waste time reinventing the wheel again and again! So, let’s begin by covering why the existing voting methods being used should be discarded. Once we have all arrived together on the same page, it will be easier to move forward with identifying a solution that truly works.
VOTING METHOD VULNERABILITIES
The ways in which each voting method used in US elections can be manipulated are outlined below.
Vote-by-Mail
At least 22 states in America use Vote-by-Mail ballots to varying degrees, three states use mail-in ballots exclusively and a fourth state, California, will use them exclusively in 2018 (according to the National Conference of State Legislature (NCSL)) .Vote-by-mail ballots are vulnerable to fraud and manipulation at nearly every level. The ways Vote-by-Mail ballots can be manipulated include:
- Voter intimidation: Friends, family members, religious groups, or political groups may threaten, coerce, or intimidate individuals into proving they have filled out their ballot in the manner they demand. This has potential to make it impossible for many individuals to vote their own will for fear of the consequences (I.e. divorce, loss of a job, ex-communicated from a community worship place, etc.).
- Vote buying: Persons are paid to fill in their ballot per the payee’s instructions.
- Ballot box stuffing: One person inserts multiple ballots into the ballot box. This can be accomplished in different ways. One example being that a poll worker can fill in ballots for persons on the voter register who did not cast a vote.
- Inconsistent Treatment of Ballots: People who count the ballots can treat them inconsistently, employing standards that change from precinct to precinct and from hour to hour, ranging from how the ballot was marked to the acceptance of voter’s signatures.
- Signatures on Ballot: Persons who check the signatures are NOT signature experts, leaving the door wide open to bias, resulting in thousands of disenfranchised voters. Let’s delve a bit deeper here. The error-prone signature verification process results in thousands of disenfranchised voters per county. The key word here is “county.” This is not per city or state, but per county! For example: In the 2007 elections, 7,677 absentee ballots were reportedly rejected in King’s County Seattle; 2,500 in Miami-Dade County Florida; 2,100; in Broward County Florida, and 1,400 in Palm Beach just because of problems with the signature. Hey! Maybe YOUR ballot was thrown out! If you can’t prove they are actually counting your vote, what is the point in researching the candidates and submitting your ballot? It’s comparable to dumping your ballot into a wishing well…and then crossing your fingers.
- Vulnerable Tabulators: It has been proven that the electronic tabulator machines oftentimes used to count the ballots once they arrive at the polling station can be hacked. Many of the tabulators provide no voter verifiable audit paper trail (VVAPT) at all, making it impossible to prove whether the outcome is valid or not. Even for those tabulators that do provide a VVAPT, it has been shown that the VVAPT can be manipulated as well. Visit Wikipedia’s page on optical scan voting to learn more.
- Broken Chain of Custody: Some post offices do not control the incoming mail for elections. Instead a private company sorts incoming absentee ballots into precincts before giving them back to the county for counting, breaking down any chain of custody rules! To learn more about this and other vulnerabilities in the vote-by-mail process, visit this website: The No Vote by Mail Project
- Ballots Arrive Too Late: Thousands of absentee mail-in ballots were reportedly rejected per county in Florida in 2012 because they arrived after the deadline. Sometimes the reasons for this are readily explainable, other times not, leaving plenty of room for pause. For example, one gentleman and his wife put their ballots in the mail together and one arrived nearly a month before the election and was counted and one arrived a day after the election and was not counted.
Optical Scan Voting
Optical scan voting (also known as Optical Mark-Sense Scanning) entails feeding a paper ballot a voter has marked into a machine that scans and tallies the votes. This is often touted as being one of the safest forms of voting, but it too can be manipulated in different ways, which include:
- Votes Credited to Someone Else: Hackers can gain access to the voting system configuration files and credit one candidate with votes intended for another. Douglas W. Jones of the University of Iowa reports this can easily be accomplished by a person with computer knowledge who is involved in setting up the election. Visit Wikipedia’s page on optical scan voting to learn more.
- Ballot Box Stuffing: Some e-voting machines provide a paper receipt. The Voter Verified Paper Audit Trail (VVPAT) receipts are printed on a paper roll behind glass. It has been shown that the voting machine can be programmed to print additional paper receipts unobserved in between voters, effectively implementing a form of ballot box stuffing. (Learn more.)
- Invalidated Ballots: An alternative way to manipulate the VVPAT count is to invalidate the printed record after the voter leaves and then print a new fraudulent ballot. These intentionally invalidated ballots would be undetectable because invalidated ballots are quite common during elections due a voter making an error and requesting a new ballot. Visit Wikipedia’s page on optical scan voting to learn more.
- Manipulate Tabulation Memory Cards: Harri Hursti, a Finnish computer programmer, demonstrated it is possible to manipulate the memory cards of machines being used to tabulate the votes.
- Playing the Odds: Video recordings have shown that most voters do not check the VVPAT receipts on the paper rolls behind the glass to confirm the vote they cast was recorded correctly, prior to submitting their vote — in spite of the computer requesting them to do so. A person armed with this knowledge could request the software to switch a certain percentage of the votes cast for one candidate to a different candidate, assuming that the majority of the time the manipulated votes would go unobserved. To help best ensure this scam went undetected, a hacker would just need to set it up so that the vote was never manipulated two times in a row. That way if an aware person checked the receipts, found an error, and recast their vote, they would be assured to see the votes they truly wanted to cast the next time, thereby reducing suspicion that the system was automatically programmed to flip votes.
- Overwrite Votes: Some VVPAT systems are technically able to reverse the paper feed. These could be open to manipulated software overwriting or altering the VVPAT even after the voter checks it. (Learn more.)
- Voter’s Intentions Misunderstood: Vote tabulator machines can misread paper ballots due to multiple types of errors made by voters when filling in the ballots, resulting in a person’s vote being discarded. Errors can include: using the wrong color or strength of ink; not filling in the oval fully; marking the ballot with a check or an X instead of coloring in the bubble; crossing out a selection & choosing something else, etc.
- Manual Audits Useless: A manual recount/audit of the paper receipts (VVPAT) could be requested, but if the computer were programmed to engage in a form of ballot box stuffing, there would be no way to know if the manual vote count is correct, rendering it useless.
- Unaffordable Recount: Actually performing a manual recount of the voter register is said to be so labor-intensive and expensive that it is unaffordable to most candidates seeking it. Armed with this knowledge, a candidate with more money could engage in election fraud, knowing candidates with less money wouldn’t have the funds to prove it occurred anyway. (Learn more.)
- No Consequences: Even if recounts of optical scan voting machines are performed and they show blatant inconsistencies, nothing happens, rendering the audit to be a virtually useless, futile endeavor. See: Michigan Recount Exposes Voting Machine Failures.
- Chain Voting: This form of fraud is initiated via a person going into a polling station, receiving a blank ballot, then leaving the polling station with the ballot in hand without casting a vote. The person proceeds to fill in the ballot off site and offers to pay another person money to go to the polling station, deposit the one that is marked in the optical scan voting machine, and to return with a new blank ballot to receive payment. This procedure can be repeated an infinite number of times.
- Counterfeit Ballots + Chain Voting: Counterfeit copies of blank ballots can be made and filled in. Money is then offered to persons to deposit a pre-filled ballot into the optical scan voting machines. To receive payment, they must return with the blank-unused ballot they received at the polling station. Visit Wikipedia’s page on optical scan voting to learn more.
Electronic Voting (also known as e-voting)
E-voting comes in two different forms: Persons can cast a vote using e-voting machines located at polling stations or vote remotely via the internet (also called i-voting). Ways these forms of voting are vulnerable are outlined below.
- Software Can Be Manipulated: Software of e-voting machines can be manipulated to add malicious code altering vote totals to favor any candidate: It can change a vote, count a vote twice, not count a vote at all, or it can lose votes. (“Electronic Voting Machines are Broken & Here’s the Code to Prove It”)
- Source Code is Owned by Private Companies: E-voting machines used in US elections are owned by private companies. They have reportedly not only refused to disclose or allow public examination of their source code, but also refused to reveal their revenue and profits.
- Software Unprotected: Software currently used by US electronic voting systems (such as the Sequoia Voting Systems) has been left unprotected on publicly available servers, leaving it open to being hacked by persons located inside or outside of the US.
- Lack of Paper Trail: Most e-voting machines do not provide an auditable, authenticatable paper trail at all and even for those that do, the paper trail can be manipulated as discussed in the Optical Scan Voting section above. Visit the Wikipedia page on Voter Verified Paper Trails to learn more.
- Voter intimidation: When e-voting is performed from personal devices at home (also known as i-voting), then friends, family members, leaders of religious or political groups may threaten, coerce, or intimidate an individual into voting in a certain manner and require proof they filled their ballot in in the manner demanded. This has potential to make it impossible for many individuals to vote their own will for fear of the consequences (I.e. divorce, loss of a job, ex-communicated from a community worship place, etc.).
- Vote buying: I-voting performed using personal devices at home leaves the door open to persons being paid to fill in their ballot per the payee’s instructions.
This 3 min video quickly and effectively highlights some of the ways electronic voting methods are unreliable: Electronic Voting Systems: Do They Improve the Voting Process? At the annual Defcon computer security conference held in July of 2017, it took hackers as little as 90 minutes to hack the e-voting machines presently being used in our elections, some of which could be hacked in mere minutes. Sadly, this is not the first time a contest of this nature has been held. These contests have been held since as early as the 2000 election and the results are always the same. Again and again they indicate: Yes. The e-voting machines used in US elections are easy to hack.
There are articles present online, such as “How to Hack an Election in 7-Minutes” that state hacking the e-voting machines in the US is child’s play for computer hackers. Furthermore, step-by-step instructional videos can be found online showing how to hack the e-voting machines being used in US elections, including how to remove the screws and insert a new chip to hack an e-voting machine’s so-called voter-verified, auditable paper trail. Examples can be viewed here: UCSB Security Attack on Voting Machines and USCB Security Group’s Attack on Voting Machines.
The simple truth: Any election system held online will be hackable. Even if it cannot yet be hacked at this precise moment — it will be hacked at some time. Hospitals, banks, government computers, and blockchain-based cryptocurrency have all been hacked and continue to be hacked. If we cannot maintain the security of these vital systems online, why would an online voting system be any different? Experts who are currently pushing for the use of electronic voting methods will rightfully argue that the vote counts can be stored simultaneously in different data centers which will make it “harder,” (but still not impossible) for someone to manipulate the vote count and have it go undetected.
An even greater concern to address with respects to holding elections online, however, is that there is no way to 100% guarantee a voter’s identity cannot be traced to the vote they cast. This is due to the multitude of entangled technology-based tracking mechanisms, which can include: GPS tracking in phones and computers, digital timestamps, the IP address may be recorded when a website is visited, or use of a stingray device to perform a man-in-the-middle attack.
A clever hacker could foreseeably gather and sell information about voters and the votes they cast online on the blackmarket, making people afraid to cast votes for certain candidates or issues out of fear of being retaliated against by groups with strong opposing viewpoints. This detail alone should be a complete showstopper for the implementation of e-voting.
Alas! It is beginning to sound rather bleak in regards to there being ANY voting method that can truly keep votes secure — but not to worry! A simple, effective way to keep both the voter’s identity and the vote count secure does exist. Keep reading.
Paper Ballots
Paper ballot elections can be conducted using three different methods, two of which are insecure and ONE of which provides a truly secure means of casting and counting the vote. The three methods are summarized below.
- Vote-by-Mail Paper Ballots: Paper ballots can be filled in at home and sent through the mail. This method of conducting paper ballot elections is vulnerable to fraud at many levels from voter intimidation, to chain voting, to ballot box stuffing, and more. See the “Vote by Mail” section above for more details.
- Paper Ballots Cast in Person & Counted by a Machine: Paper ballots can be filled in at a polling station and then fed into an optical scan voting machine. Optical Scan voting machines are hackable, making this a suboptimal solution for keeping the vote counts secure, especially in states with no guidelines for mandatory audits. See the section above on “Optical Scan Voting” to learn how electronic tabulator machines are vulnerable.
- Paper Ballots Cast in Person and Hand Counted the Same Day: Paper ballots that are cast by voters in person and counted on the same day provides a valid means for holding a secure election because the entire process can be observed and monitored from the beginning to the end.
Let’s take a closer look at the ways elections held using paper ballots have “potential” to be vulnerable. These are summarized below:
- Chain Voting: A person can steal or create a counterfeit copy of a blank ballot; fill it in, and then pay another voter to deposit it in the ballot box at the polling station, instructing the person to bring back the blank ballot they received at the polling place to receive their payment. This procedure is repeated again and again an infinite number of times.
- Ballot box stuffing: Involves placing multiple ballots into a ballot box. This can be accomplished in different ways, one of which is for a poll worker to fill in ballots for persons on the voter register who did not shown up to vote.
- Ballot Marking: This can be accomplished by placing a black marking device under a fingernail for use in marking the ballots. Persons who count the ballots can add an additional mark beside a 2nd candidate’s name for the same office thereby invalidating the original vote cast (because counters cannot discern the voter’s intention) or make additional marks beside issues the voter themselves may have chosen to leave blank in order to increase the vote count for the candidates and/or issues they like best. They can also intentionally mark a symbol on ballots because ballots with identifying symbols present are not counted (to prevent vote-buying scams.)
Each of the 3 vulnerabilities listed above, however, can be readily eliminated via strict adherence to a simple sequence of steps when administering paper ballot elections, which includes, but is not limited to
- using a clear ballot box that allows everyone to see the box is empty at the start of the day (the ballots will be folded in thirds before being dropped inside to ensure the votes cast are not visible).
- having poll workers initial the back of all ballots on their ballot pads at the start of the day and to check that their initials are present on the ballot before the voter drops the ballot into the ballot box
- having a prefixed number of polling station observers present at each polling station (a combination of people appointed by each major political party, volunteers from the public, and international election observers)
- video recording of all counting procedures that occur from the moment a polling station’s doors close to the public.
Further ballot and vote counting process details can be found in the document “Procedure for Conducting and Counting Paper Ballot Elections.” [Add Link].
Canada and our own state of New Hampshire both hold paper ballot elections in which the votes are cast and counted the same day, proving it is feasible to conduct an election in this manner. Based on online reports, they are able to count the votes in an average of 2-3 hours. So, if the polls were to close at 8:00 PM, the vote counting could easily be wrapped up by midnight of Election Day.
More details on the administration of paper ballot elections can be found on the page devoted to “Solutions to Secure the Vote,” including ways to address veterans voting from abroad, disabled voters, and more. The link to that page can be found at the end of this document. We encourage you to continue reading below first before visiting it, so you’ll have a full grasp of the vulnerabilities in the current voting systems and have a good grasp of what has already been tried across our country and the world to attempt to make elections secure.
Hybrid Systems: Paper Ballots & E-Voting
Some places have tried hybrid voting systems that combine paper ballots and e-voting. One such example involves requiring voters to cast their vote in a public polling station using an electronic voting machine, which then produces a paper receipt with a barcode as proof of the vote cast. This method does not increase the safety of the vote!
Why? Because a voter could select a candidate’s name (I.e. Gary Johnson) on the computer screen and observe that the computer placed a green check by his name. The software running in the background, however, could be set up to credit every third vote received for Gary Johnson as a vote for Donald Trump and to print a corresponding barcode for “Donald Trump.” Since the voter has no way of knowing what the barcode says, they would be none the wiser this had happened. If an audit were requested, the computer tally and the receipt barcode tallies would actually match – even though they did not record the actual vote the person intended to cast.
What if there was a second, separate device present at the polling station that allowed voters to privately scan the barcode to ensure it indeed recorded the vote they cast?This idea is suboptimal for the following reasons: It creates more expense, adds more technology that can break down in the middle of election day causing unnecessary chaos and long lines, requires additional poll worker training, and opens the door to a voter intentionally lying that the vote they truly cast and the scanned vote do not match to intentionally undermine the perceived integrity of the election process.
Another hybrid voting method presently being used is the combination of paper ballots and optical scan voting machines. Using a machine to count the paper ballots will, on average, obviously make it easier and faster to count the votes, but… the Optical Scan machines can be hacked, as outlined under the section above on “Optical Scan Voting,” making this solution suboptimal. The machines themselves can, do, and will break causing long lines at the polls. They will continually need to be upgraded over the years (costing taxpayers millions). Thousands of Poll Workers will be required to undergo training prior to each election to learn (or relearn) how to use them — adding yet even more cost. Reminder: Our country is trillions in debt.
In contrast, an election conducted in which the votes are cast in person and counted by hand can be conducted in a fraud-free manner (using teams consisting of persons from opposing parties). It does not rely on machines that would break midday and disrupt the election process. There would be no equipment to continually replace over the years. The paper ballots can be counted by hand using volunteers who are trained onsite (within as little as 10 minutes) and the vote count can be completed in 2-3 hours. It is even possible to perform a 2nd count (an audit) at the same time. Easy peasy!
- So, here’s a grand idea: Let’s nix the machines!
- End result: Elections will be secure, simple, cheaper, and easier to maintain.
DOES OUR MESSY ELECTION SYSTEM MAKE IT HARDER TO HACK?
People have argued the mere fact that we have a jumble mix of voting systems in place across the US makes our elections more difficult to hack. There is some truth in that, but – it only goes so far. It is not necessary for someone to understand how to manipulate every voting method in order to swing an election in our country. It is just necessary to understand how to manipulate a certain percentage of the voting methods to tip the scales.
All of the vulnerabilities for the different voting methods being used in the US are already well known and extremely well documented both online and in books, so it would not take a clever person much time or energy to figure out how to swing an election in our country.
People have further argued that our elections must surely be difficult to hack due to the sheer volume of different polling places, ultimately making it too difficult for anyone to know where to direct their efforts. Nope! Even this aspect has been thoroughly researched. The information is readily available online for anyone to see. For instance, there are simple tools, like the Swing-o-matic tool found in the article“What Would It Take to Turn Red States Blue or Blue States Red?”, which very nicely and clearly shows the mathematical breakdown & demographics for what it would take to swing a US election.
There are also an abundance of detailed maps present online, such as the maps shown below, which clearly lay out the types of voting systems that exist and where they are being used, making it extremely easy for someone seeking to manipulate our elections to plot a plausible course of action to undertake when doing so. The first screenshot below shows a map that is visible on the Pew Research Center website.
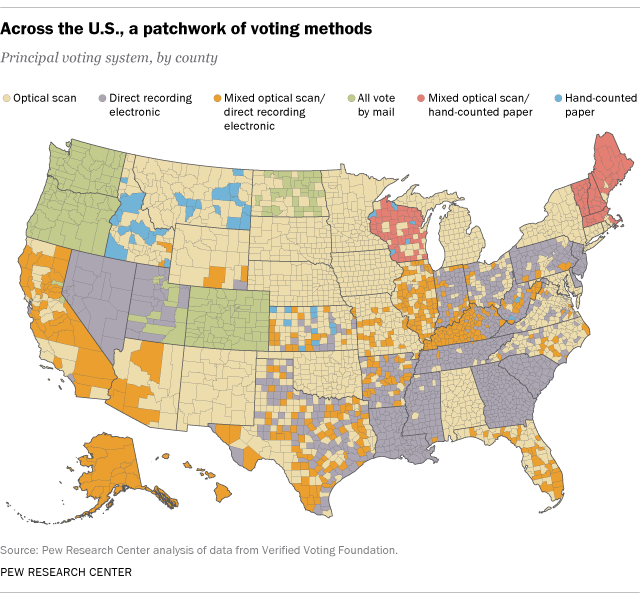
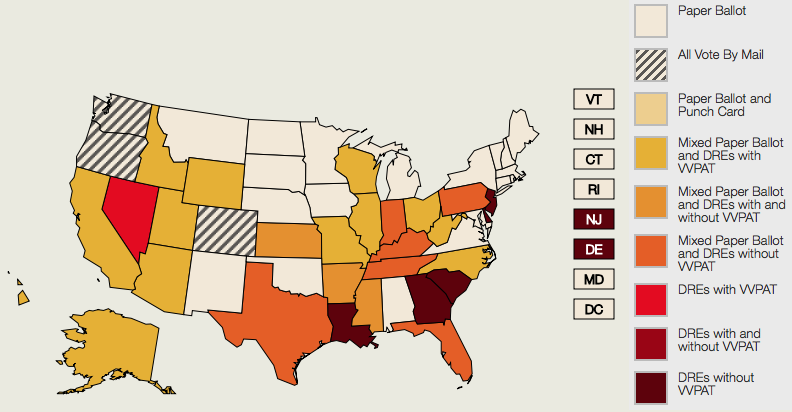
Furthermore, there is information readily available online clearly outlining the types, manufacturers, models, and characteristics of voting machines being used in US elections. For example, VerifiedVoter.org shows a map (See example in the screenshot below.) that allows viewers to identify the exact type, make, and model of equipment that is being used in each precinct. By clicking on a state on the map present on Verified Voter’s website a reader gets directed to a page with an extremely nicely organized table that lists the exact make, model, and brand of equipment used per county.
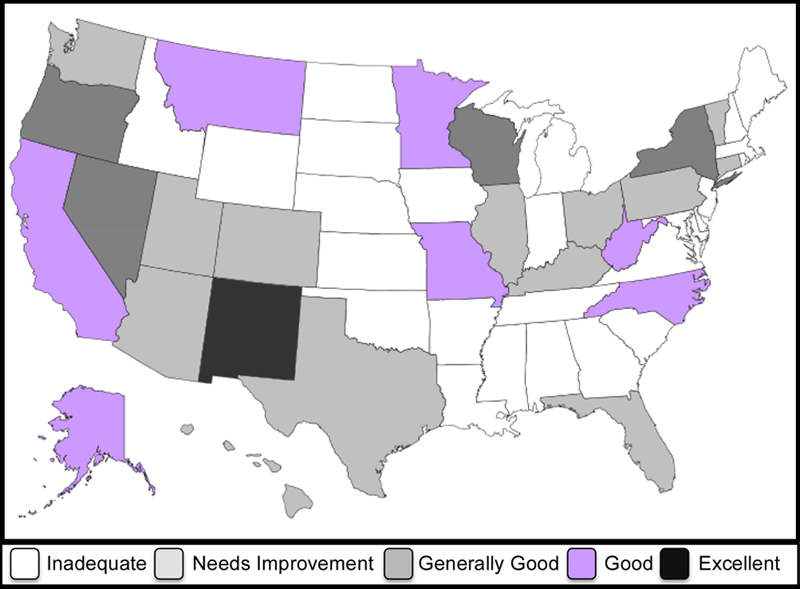
VerifiedVoter.org also has a map identifying which states have good audit methods in place and which do not, making it easy to select areas with poor audit systems as targets for hacking.
A RECIPE TO HACK AN ELECTION
So, how hard would it be for someone to manipulate an election in the US?
A political party or group that is seeking to flip an election in our country needs to have an understanding of two components: voting methods in use and the demographics of the different areas. This information is already well researched and is readily available online, as outlinedabove. So, the next step is to identify an action plan to achieve the desired election results. One such recipe for flipping an election might be:
- Manipulate a percentage of the readily hackable e-voting machines, targeting in particular those that do not have a paper trail. As noted in the section above on Electronic Voting, the methodology for hacking each of the machines can be found in books and online in step-by-step videos, so hacking the machines should be a piece of cake for anyone with computer knowledge.
- Provide misleading information to voters in select geographic areas via robocalls, telling them the voting day or their polling location has changed or giving them misleading information about voter registration dates and ID laws. This practice appears to happen often in our elections and even repeatedly so in Texas, per the Brennan Center for Justice.
- Intentionally deposit broken e-voting machines in select geographic locations, resulting in ridiculously long lines and in turn cause many people to give up and go home. In nearly every election there are reports of people being forced to wait in lines for up to 5 hours or more just to cast a vote. Up to 75% of the machines were broken in one county alone in Utah in 2016.
- Reduce the number of available polling stations in geographic areas that are likely to vote for the opposing party. Southern states closed 868 polling places in 2016.
- Add to this mix a calculated, slow, steady drip of misleading media propaganda about the candidates and issues.
This is just one course of action that is easy to envision. A more clever person could surely envision even better recipes than this for swinging an election.
PERCEPTION OF ELECTION INTEGRITY
There is a visibly growing mistrust in the integrity of American elections from people on both sides of the political aisle, which is extremely dangerous given the increasingly heated political climate inside our country.
- According to a Gallup survey released in March 2016, only 3 in 10 Americans believe that the nation’s process for electing a new president is functional, some 66 percent believe that the system is broken, while 4 percent had no opinion.
- Nathaniel Persily, a professor at Stanford Law School and Jon Cohen, the chief research officer for SurveyMonkey conducted a survey of 3,000 people in October of 2016 (just prior to the last presidential election). American citizens were asked if they would accept the result should their candidate lose in November. Only 31 percent said they definitely would see the outcome as legitimate. Nearly as many (28 percent) said it was “unlikely” that they would accept the result or that they definitely would not.
- The SurveyMonkey poll further showed that 40% of Americans reported they had lost faith in American democracy itself. More than 6 in 10 voters backing Democratic nominee Hillary Clinton expressed a lack of faith in U.S. democracy, and over 4 in 10 of those backing Donald Trump. More polling details can be found in the article: Americans are losing faith in democracy.
The poll results mentioned above were conducted prior to the 2016 presidential election. Since that time, President Trump has continued to attack the integrity of the US elections. He stated he was the victim of widespread voter fraud and that he actually should have won the popular vote, but did not because millions of undocumented immigrants voted for Clinton. He further claimed 3-5 million undocumented immigrants voted illegally in the state of New Hampshire, which was won by Clinton. These claims have thus far been unsubstantiated, but the fact that our elections are such a hodge-podge mess leaves the door wide for many voters to doubt the outcome of the elections is legitimate.
LET’S FIX IT!
Proposal: Let’s come together and fix our elections – American-style!
America is a country full of the best and brightest people. When brilliant minds unite together, great things emerge: computers, smartphones, self-driving cars, and reusable rockets to name just a few. Setting up a streamlined, secure voting system that protects each individual’s vote is arguably a piece of cake in comparison!
Faith in elections is a cornerstone to a healthy, functioning democracy. A critical key to fixing our elections is to choose a secure method for casting and tabulating the votes. Based on the information presented above, to date it appears there is only one viable method that will keep the vote itself secure, which is to cast votes on paper ballots and count them the same day.
The Good News: Paper ballot elections are both simple and easy to administer, as well as cheap to conduct and maintain. Excellent! This is a win-win in every respect. To learn more about the elements that need to be addressed when administering a paper ballot election, visit [Add Link].